Why is Vulnerability Assessment Essential?
Digital Security What's more, in exceedingly controlled businesses like the fund, medicinal services or people in general segment, guaranteeing the wellbeing of your item is a vital prerequisite illustrated in models and directions, including ISO 27001, PCI DSS, HIPAA, CCHIT and numerous other compulsory principles. Conforming to these is fundamental for each player in those enterprises.
Spiral World Security Services
Spiral World offers its customers a defenselessness appraisal benefit, which is a far-reaching assessment of a framework for uncovered vulnerabilities without their immediate abuse. Savvy, general helplessness evaluations can be a valuable apparatus in remaining up and coming with regards to security.
An application-level helplessness appraisal is an ideal fit for items amid the late advancement arranges before they achieve generation. It can be viable finished in a test situation and help to make your item secure in time for discharge. For discharged applications, both helplessness appraisals and entrance testing can help guarantee most extreme security consistently.
Spiral World performs helplessness evaluations as per "best-in-class" hones as characterized by ISECOM's Open Source Security Testing Methodology Manual (OSSTMM) and the Open Web Application Security Project (OWASP). Our specialists utilize both computerized devices and manual methods to recognize vulnerabilities that debilitate to trade off the security of delicate data ensured by a customer's foundation, arrangements, and procedures.
Because of the evaluation, Spiral World gives an extensive report containing distinguished dangers, security shortcomings, and misconfigurations and additionally particular, noteworthy strides to kill recognized vulnerabilities and enhance general security.
Service Highlights
Vulnerability evaluation can help:
- Identify Security Issues Before They Can Be Exploited;
- Improve Productivity By Avoiding Application Downtime;
- Protect The Integrity And Confidentiality Of Sensitive Enterprise Data;
- Ensure Security In Time For Product Release.
By taking preventive measures, you can eventually spare a large number of dollars in misfortunes from bargained notoriety, decreased client certainty, business disturbances, lost efficiency and that's just the beginning.
Typical Workflow
The workflow for vulnerability assessment involves the following stages:
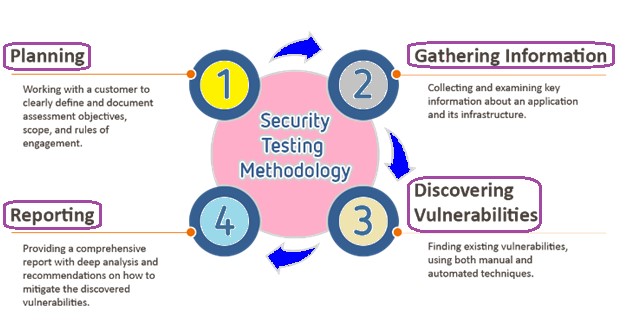
The work process is fundamentally the same as infiltration testing, with the significant distinction concerning the way toward finding vulnerabilities. While entrance testing is a genuine assault reproduction, amid helplessness appraisal our specialists don't abuse any of the vulnerabilities found. The Spiral World group utilizes both robotized devices and manual strategies just to find existing vulnerabilities.
